
Microsoft is automatically enabling Windows Extended Protection on Exchange servers after installing this month's 2024 H1 Cumulative Update (aka CU14).
Extended Protection (EP) will automatically be toggled on by default when installing Exchange Server 2019 CU14 (or later) to strengthen Windows Server auth functionality to mitigate authentication relay and man-in-the-middle (MitM) attacks.
"This will happen when running the GUI version of Setup and when running the command line version of Setup without using either the /DoNotEnableEP or /DoNotEnableEPFEEWS setup switch to opt out," said The Exchange Team.
"If your servers are not ready for using EP (for example, they use SSL bridging or there are mismatches between client and server TLS configuration), and you do not opt out of EP enablement during Setup, it is possible that some functionality may break after installing CU14."
Admins are advised to evaluate their environments and review the issues mentioned in the documentation of the Microsoft-provided ExchangeExtendedProtectionManagement PowerShell script before toggling EP on their Exchange servers (this script automatically updates itself on systems connected to the Internet).
If encountering issues after EP is enabled, admins can either ensure that all EP prerequisites are met or use the script to turn off the feature.
They can also enable EP on older versions of Exchange Server (i.e., Exchange Server 2016) using the same PowerShell script on online servers.
Redmond also released the simple-to-follow decision flow graph embedded below to help those who still need to enable it to further secure their Exchange environment.
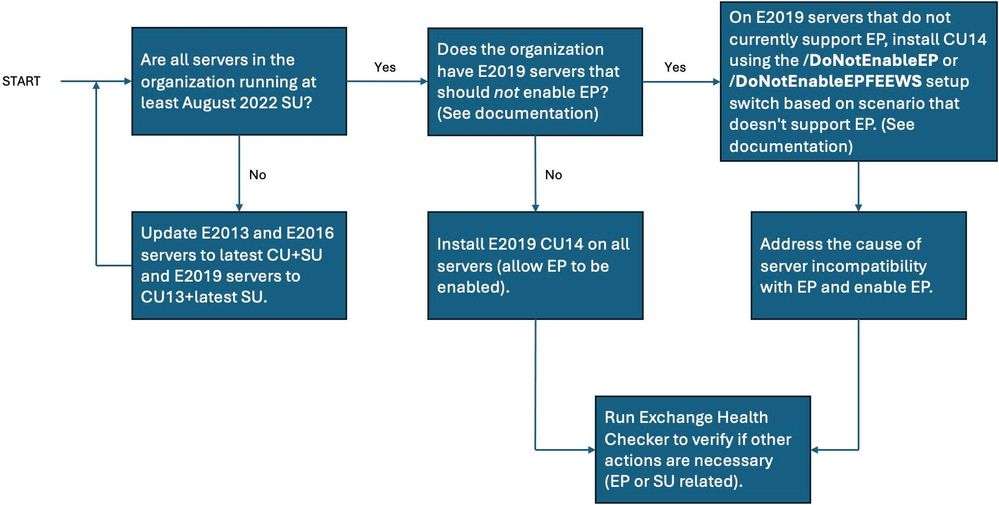
Microsoft first introduced Exchange Server EP support in August 2022, with cumulative updates released as part of the August 2022 Patch Tuesday when it fixed several critical severity Exchange vulnerabilities (CVE-2022-21980, CVE-2022-24477, and CVE-2022-24516), allowing for privilege escalation.
Redmond said that, besides patching these bugs, admins would also have to enable Extended Protection to ensure that attackers won't be able to breach vulnerable servers.
The same request was made this Tuesday to fully address the CVE-2024-21410 vulnerability allowing remote threat actors to escalate privileges in NTLM relay attacks.
One year later, the company announced that Exchange Extended Protection would be enabled by default on all Exchange servers after deploying CU14.
Microsoft's recommendations shared in August 2023 and dependent on what security update is installed include:
- Aug 2022 SU or later and EP enabled: Install CU14 (no special steps needed).
- Aug 2022 SU or later, but EP not yet enabled: Install CU14 with the default of 'Enable EP' left on.
- Exchange Server version earlier than the Aug 2022 SU: "We send you thoughts and prayers, and very strong but gentle guidance to update your servers to the latest SU immediately."
"We recommend that all customers enable EP in their environment. If your servers are running the August 2022 SU or later SU, then they already support EP," The Exchange Team said in August 2023.
"If you have any servers older than the August 2022 SU, then your servers are considered persistently vulnerable and should be updated immediately. Further, if you have any Exchange servers older than the August 2022 SU, you will break server-to-server communication with servers that have EP enabled."
Microsoft also urged customers one year ago to always keep their on-premises Exchange servers up-to-date so they're ready to deploy emergency security patches.
"exchange" - Google News
February 15, 2024 at 12:34AM
https://ift.tt/cGZ96Xi
Microsoft Exchange update enables Extended Protection by default - BleepingComputer
"exchange" - Google News
https://ift.tt/EuPhbrL
https://ift.tt/UFi8OwY
Exchange
Bagikan Berita Ini














0 Response to "Microsoft Exchange update enables Extended Protection by default - BleepingComputer"
Post a Comment